The New System: Netfilter
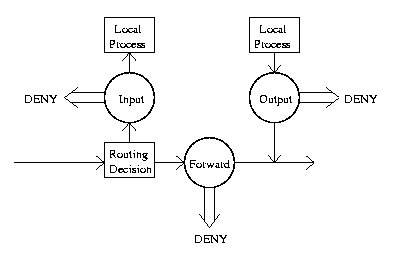
pre-routing demasquerade, reverse NAT, redirect
input packet filtering, local unreverse NAT
forward packet filtering
output packet filtering, local reverse NAT
post-routing masquerade, de-reverse NAT
- Each hook can be registered for by multiple modules; numerical priority determines ordering.
- Can return NF_DROP, NF_ACCEPT, NF_QUEUE (or NF_STOLEN).
- NF_ACCEPT
- Continue traversing next hook.
- NF_QUEUE
- Queue for asynchronous (eg. userspace) processing.
- NF_DROP
- Free the skbuff, forget about packet.
- NF_STOLEN
- Forget about packet.
- The next hook on that hook point called unless NF_DROP or NF_STOLEN returned.
- Caching bitfield indicates what that hook examined, and if it
changed the packet.
Packet Filtering
- New filtering tool and extensible module called `ip_tables.o'; uses
hooks input, forward, and output.
- Example modules: REJECT module (sends ICMP port unreachable and
returns NF_DROP), and MAC module (compares MAC address).
- Loads whole tables instead of individual rules.
- Smaller than ipchains.
- Knows nothing about packet manipulation (eg. masquerading, NAT or
redirection).
Connection Tracking
- Module `ip_conntrack.o' provides tracking of local and non-local connections.
- Uses hooks pre-routing and output.
- Each packet is considered to be part of a connection if possible.
- Connections have various `states'.
- Required for NAT, useful for packet filtering.
- Can view connections in /proc/net/ip_conntrack
- Module exists to understand FTP PORT and PASV response.
Masquerading/NAT
NAT: Network Address Translation
- Alter source IP to make outgoing packets appear to come from
somewhere else.
- Alter destination IP of incoming replies to return to original
source.
NAPT: Network Address Port Translation
- As above, but with awareness of protocols, so we can shuffle
source ports to overload multiple IPs onto one IP.
- We don't differentiate between NAT and NAPT: we always to NAPT
where we need to, and understand the protocol.
Masquerading
- As above, but source IP used is IP address of the interface
the packet is being routed to.
RNAT: Reverse NAT
- Alter destination IP of incoming packets to direct it to real
server.
- Alter source IP of replies to come from where the client expects.
- Exactly the same as NAT, but connection setup is initiated by
an "incoming" not "outgoing" packet.
- New NAT infrastructure uses hooks pre-routing, post-routing, input and output.
- Provides mangling of ICMP, TCP and UDP by default.
- Modules can be written for other protocols, or they can be
handled as "black boxes" (breaks most protocols).
- Different "mapping-type" modules can be written which define a new
mapping type: eg. masquerading or redirect already done..
- An ordered (most-specific to least-specific) setup table is kept,
which is manipulated by userspace. When a match is found in this
table, the optional mapping-type module is called to alter the connection.
- Module exists to mangle FTP data.
Next

